Cyber threats are expanding rapidly, and organizations across the globe are struggling to manage the crisis. There is a desperate need to create a secure environment for businesses and customers. Developing and implementing a robust cybersecurity plan will help organizations manage and even mitigate some risks associated with digital business.
So, what is Cybersecurity risk management?
All organizations are vulnerable to cyber attacks, no matter how vital their security parameters are. Businesses need robust cybersecurity practices to manage vulnerabilities and threats effectively.
Cybersecurity risk management helps organizations analyze, review, and manage risks that have the potential to impact the operations and performance of the business.
Cyber threats are a grave area of concern. A recent article from Forbes states that data breaches alone cost an estimated $6 trillion loss globally in 2021, with the hackers targeting the systems of both small and large businesses for ransom, raising the alarm for effective cybersecurity solutions.
Having a clear assessment of your network will help you find the loopholes inside your organization, highlight the threats, and mitigate their effect before they could cause any harm.
All functions must operate with clearly defined roles and responsibilities to effectively manage cybersecurity risk.
The days of isolated departments fumbling along in disjointed confusion are long gone. Today’s risk environment requires a cohesive, coordinated, disciplined, and consistent risk management approach.
What benefits does Risk management bring?
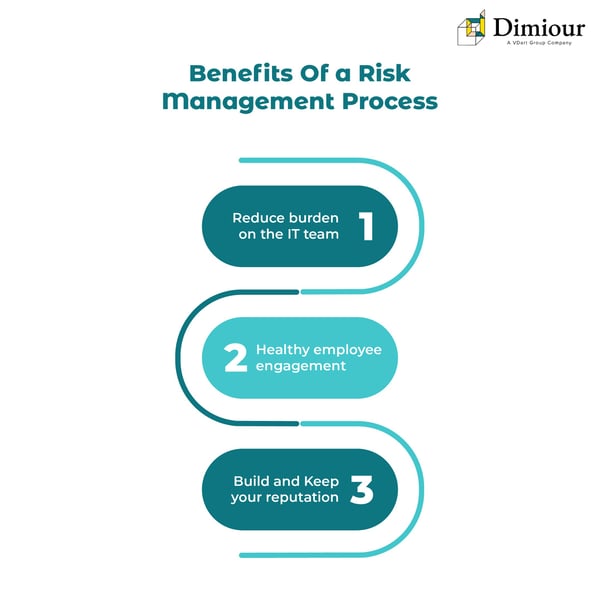
- Reducing the burden on the IT team: IT teams in an organization are responsible for keeping everything on track. With risk management in effect, it allows the IT team to have a standard set of procedures to access and deal with any crises more quickly and effectively.
- Healthy employee engagement: Data breaches commonly occur from unsuspecting employees making simple mistakes like clicking a link or opening a file in an email and exposing employee and customer information to hackers.
- Building and Keeping your reputation: Losing your brand’s reputation can be devastating. Exposing your customer’s data through a data breach can undermine any value they find from your organization. Implementing cybersecurity measures helps you to manage risk management to keep your solid reputation.
How can you effectively manage risk?
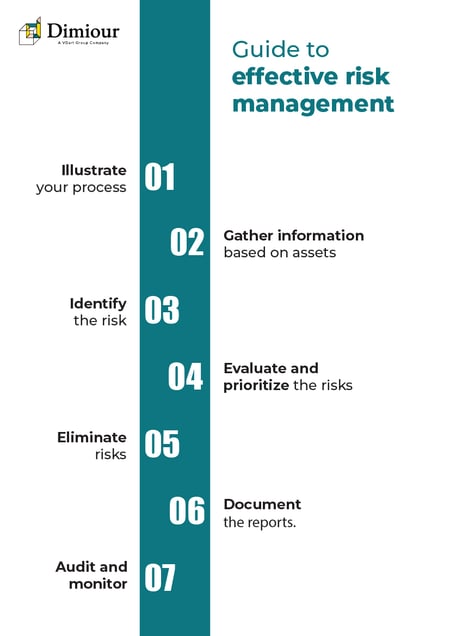
Step 1
Illustrating your process: Every organization operates on its procedure, and it is vital to plot an approach based on the specific factors of that organization. To be effective in this process, learn what your business needs, including responsibilities under agreements, rules, and other regulations, and your goals for information security. This well-established technique for evaluating hazards frequently considers their potential effect and likelihood of occurring. They must be well-defined and widely accepted to provide results comparable to any two risk assessments. Selecting your risk acceptability requirements is the final stage. You must choose the amount of residual risk you are willing to accept because you cannot eliminate all of it.
Step 2
Gathering Information based on assets: The asset-based method makes evaluation easier for organizations if they already exist in the list of information assets, which is all the organization’s data, including hard copies, media, mobiles, and electronic files.
Step 3
Identifying the risk: This is the most crucial part of the entire process as it involves a complete analysis of your data and network to anticipate impending areas under threat possibly. This can stem from within the respective teams allowing them to give their insights and be more engaged in the process since some of them might have experienced some in the past. Once you have gathered asset information, it allows you to streamline and work toward risks associated with those assets, like employees losing their organization-issued assets and possible situation of a data breach when accessing insecure internet.
Step 4
Evaluating and prioritizing the risks: Now that you’ve gathered asset information and assessed the risks. It is time to evaluate them and prioritize those risks to come to a conclusion where you need to shift your focus more. This also paves the way to pinpoint the effect it will have on certain operations if it is to happen, allowing the teams to work on a solution for all the risks based on priority. This prevents substantial delays or interruptions to the risk management workflow throughout the treatment phase.
Step 5
Eliminating risks: Teams should be deployed to dismiss or mitigate that risk so that it no longer threatens the process or the operation. Another component of efficiently managing and mitigating risk is making the most use of your team’s resources while maintaining the project’s timeline. As time goes on and your database of previous projects and their associated risk records grows, you’ll be able to anticipate future threats.
Step 6
Documenting reports: Documenting is the next step, and that is something essential for necessary certification and audits. And when it comes to documentation, the SOA ( Statement of Applicability) plays a significant part in your ISMS (Information Security Management System) . Section 6.1.3 in SOA addresses the actions that need to be taken on risks and opportunities. The SOA is an integral part of ISO27001 and helps to identify controls chosen to handle all the identified risks. Furthermore, it also provides whether the organization has implemented the rules.
Step 7
Auditing and Monitoring: Creating a risk-reduced environment is only possible when everyone in an organization works together to be more cautious with your business’ critical data and systems. Constant participation and communication between different team members in your organization is crucial for monitoring potential threats. With ISO27001 in action, your organization must monitor, review and update continuously to enhance your ISMS and ensure it is as effective as it should be. The whole process is not a one-off, but an evolving cycle with assessments done yearly to analyze strategically and stay updated in this ever-evolving threat environment.
We provide best-in-class Cybersecurity solutions for our clients to ensure that they are protected and abiding by all the mechanisms and compliance requirements. Our services help organizations to create a safe and secure environment for their data and business operations.
Implementing ISO27001 is critical and can safeguard your sensitive data and minimize its vulnerability to threats. And to implement that for your business, we offer a free risk management test for your organization to help you identify the challenges and risks affecting your business.
Get in touch with us today to learn more about how we can help you mitigate your cybersecurity risks and challenges.

